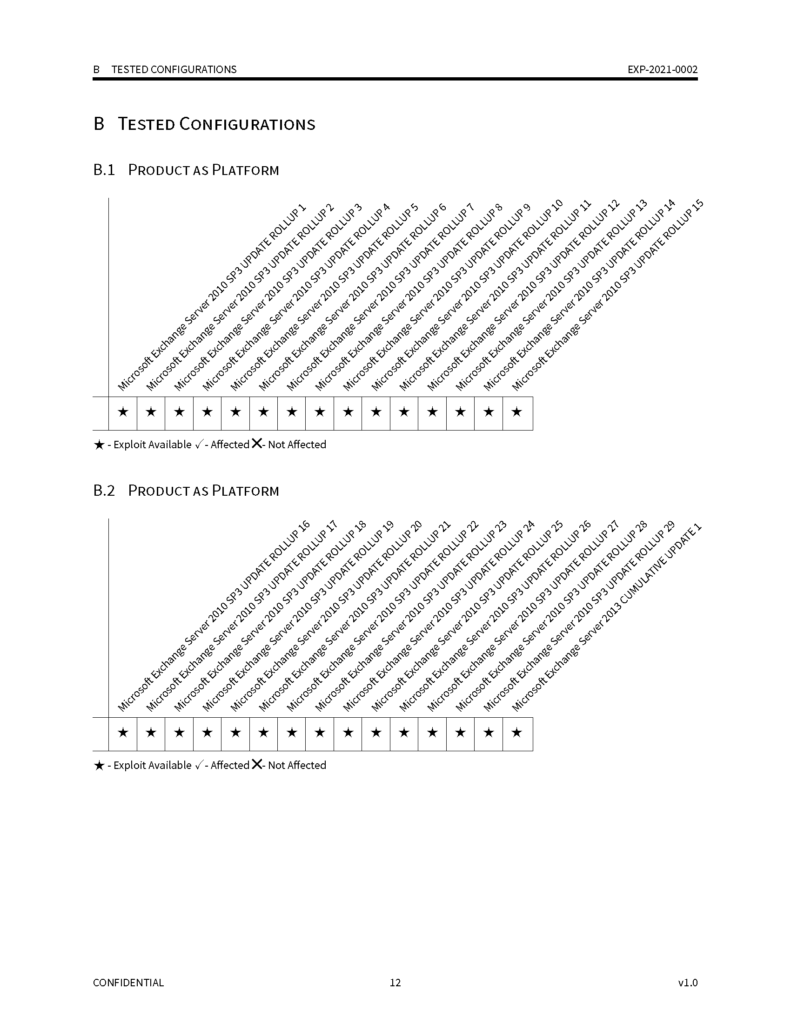
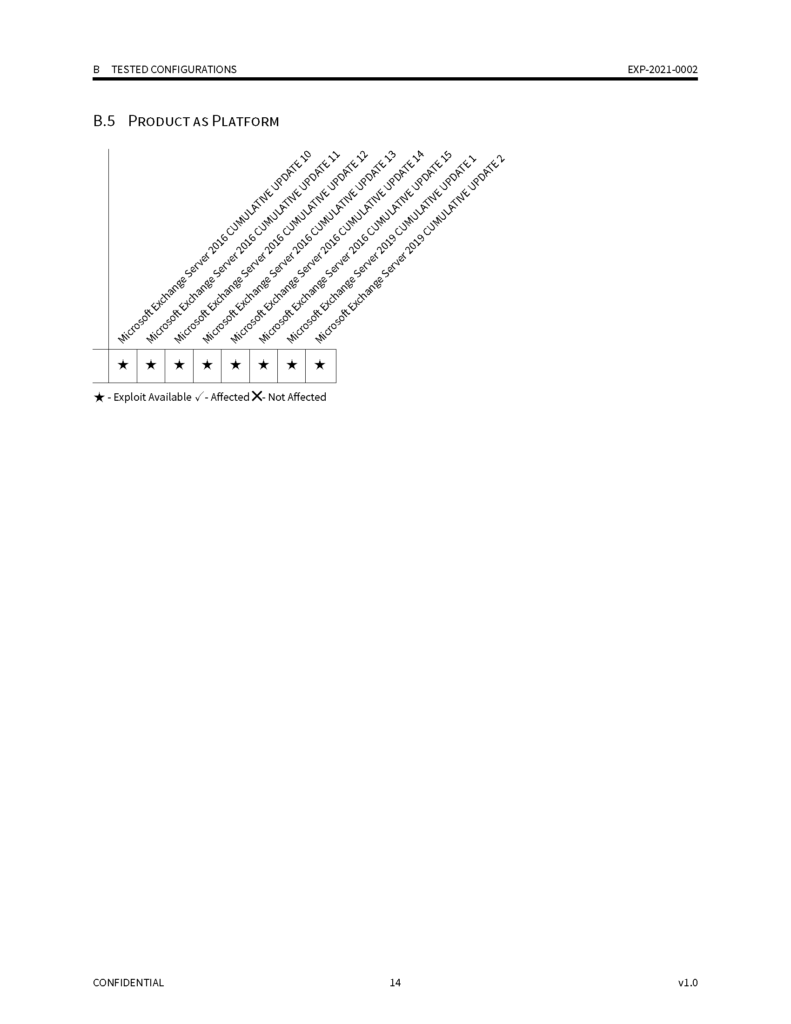
UPDATE: Postponed. Unfortunately due to travel restrictions related to COVID we will be postponing these trainings until February 14, 2022. We are contacting current registered students and giving them the option of a refund or credit and a guaranteed spot in our February class. We apologize to all those affected by this.
—
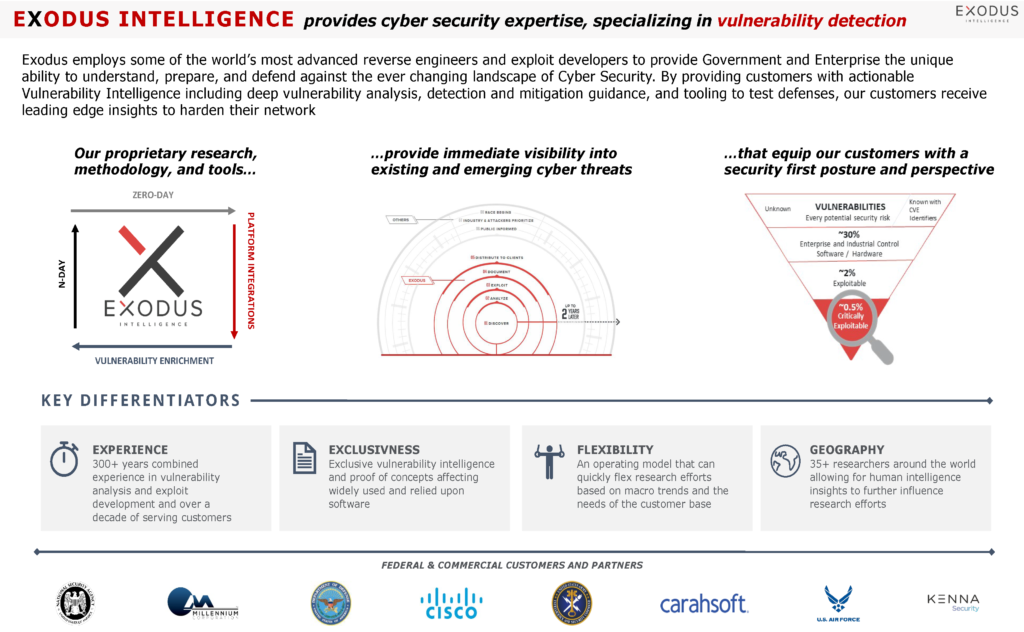
We are pleased to announce that the researchers of Exodus Intelligence will be providing publicly available training in person in early November February 2022 in Austin, TX.
In an effort to fully teach the breadth and depth of Vulnerability Intelligence and Exploitation, we have structured our offerings in the form of three distinct courses.
The intermediate course, titled the Vulnerability Assessment Class, covers a wide range of vulnerability and exploitation related topics and is intended for the beginner to intermediate level practitioner. This course is intended to prepare the student to fully defend the modern enterprise by being aware and equipped to assess the impact of vulnerabilities across the breadth of the application space.
We will also be offering an updated version of our popular Vulnerability Development Master Class. This course will cover advanced topics such as dynamic reverse engineering, kernel exploitation concepts, browser exploitation, mitigation bypasses, and other topics.
Our third offering will be our Mobile Vulnerability Exploitation Class. This class will cover advanced topics concerning mobile platforms.
Dates & Locations
All three courses will run concurrently.
November 1st-5th 2021, Austin, TX, USA- New Dates: February 14, 2022, Austin, TX, USA
Attendees should plan to travel and arrive prior to Monday, February 14th. The course work will conclude on Friday, February 18th, 2022.
Seating is limited. Since this training will be in person, there are a limited number of seats available.
Vulnerability Assessment Class
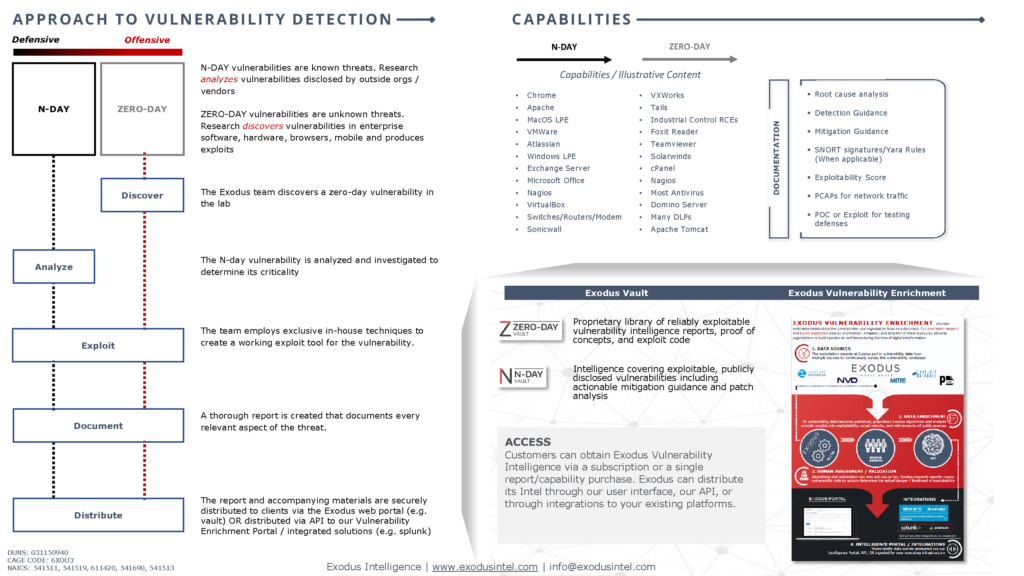
This 5 day course is designed to provide students with a comprehensive and progressive approach to understanding vulnerability and exploitation topics on both the Linux and Windows platforms. Attendees will be immersed in hands-on exercises that impart valuable skills including a deep dive into the various types of vulnerabilities exploited today, static and dynamic reverse engineering, vulnerability discovery, and exploitation of widely deployed server and client-side applications. This class will cover a lot of material and move very quickly.
Prerequisites
- Computer with ability to run a VMWare image (recommended 16GB+ memory)
- Some familiarity with debuggers, Python, C/C++, x86 ASM. IDA Pro experience a plus.
- No prior vulnerability discovery experience is necessary
Syllabus to be provided in the near future.
Pricing and Registration
The cost for the 5-day course is $5000 USD per student. You may e-mail training@exodusintel.com to register and we will supply a purchase order.
We will be providing a template request form in the near future to help justify attendance to management.
Vulnerability Development Master Class
This 5 day course is designed to provide students with a comprehensive and progressive approach to understanding vulnerability and exploitation topics on both the Linux and Windows platforms. Attendees will be immersed in hands-on exercises that impart valuable skills including a deep dive into exploiting kernel and browser vulnerabilities, static and dynamic reverse engineering, 0-day vulnerability discovery, and exploitation and workarounds of current mitigations. This is a very hands on deep dive. Course will be taught by Exodus researchers.
Prerequisites
- Computer with ability to run a VMWare image (recommended 16GB+ memory)
- Student must be comfortable with debuggers, Python, C/C++, x86 ASM, and IDA Pro.
- No prior vulnerability discovery experience is necessary
Syllabus to be provided in the near future.
Pricing and Registration
The cost for the 5-day course is $6500 USD per student. You may e-mail training@exodusintel.com to register and we will supply a purchase order.
We will be providing a template request form in the near future to help justify attendance to management.
Mobile Vulnerability Exploitation Class
This 5 day course is designed to provide students with a comprehensive and progressive approach to understanding advanced exploitation topics involving the Android operating system. Attendees will be immersed in hands-on exercises that impart valuable skills including a deep dive into the various types of vulnerabilities exploited today, static and dynamic reverse engineering, vulnerability discovery, and exploitation of widely deployed mobile platforms and applications. This course is highly advanced and will cover difficult materials. Course will be taught by Exodus researchers.
Prerequisites
- Computer with ability to run a VMWare image (recommended 16GB+ memory)
- Some comfort with debuggers, Python, C/C++, ARM ASM and IDA Pro
- No prior vulnerability discovery experience is necessary
Syllabus to be provided in the near future.
Pricing and Registration
The cost for the 5-day course is $7500 USD per student. You may e-mail training@exodusintel.com to register and we will supply a purchase order.
We will be providing a template request form in the near future to help justify attendance to management.
Covid-19 and Travel
We understand that travel conditions are constantly changing due to Covid-19. To that end, Exodus will adjust the course if necessary. If the situation arises that requires adjustment, Exodus will release an official statement and alert all registered students. In the case of cancellation, refunds (or course credit for future offerings at student’s discretion) will be provided.