Windows Sockets: From Registered I/O to SYSTEM Privileges
By Luca Ginex Overview This post discusses CVE-2024-38193, a use-after-free vulnerability in the afd.sys Windows driver. Specifically, the vulnerability is in the Registered I/O extension
By Luca Ginex Overview This post discusses CVE-2024-38193, a use-after-free vulnerability in the afd.sys Windows driver. Specifically, the vulnerability is in the Registered I/O extension
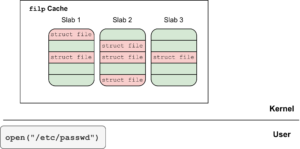
By Oriol Castejón Overview This post discusses a use-after-free vulnerability, CVE-2024-0582, in io_uring in the Linux kernel. Despite the vulnerability being patched in the stable kernel in December
By Javier Jimenez and Vignesh Rao Overview In this blog post we take a look at a vulnerability that we found in Google Chrome’s V8 JavaScript
By Vignesh Rao and Javier Jimenez Introduction In October 2023 Vignesh and Javier presented the discovery of a few bugs affecting JavaScriptCore, the JavaScript engine of Safari.
By Vignesh Rao Overview In this blog post, we describe a method to exploit an integer overflow in Apple WebKit due to a vulnerability resulting
By Javier Jimenez Overview This post describes a method of exploiting a race condition in the V8 JavaScript engine, version 9.1.269.33. The vulnerability affects the following
By Michele Campa Overview We describe a method to exploit a Windows Nday vulnerability to escape the Adobe sandbox. This vulnerability is assigned CVE-2021-31199 and
By Sergi Martinez Overview It’s been a while since our last technical blogpost, so here’s one right on time for the Christmas holidays. We describe
By Arav Garg Overview This post analyzes a use-after-free vulnerability in clfs.sys, the kernel driver that implements the Common Logging File System, a general-purpose logging
By Sergi Martinez In late June, we published a blog post containing analysis of exploitation of a heap-buffer overflow vulnerability in Adobe Reader, a vulnerability
