Container-based deployments are becoming more and more common in the enterprise, with Docker usage doubling from 2015 to 2016[1]. One of Docker’s primary strengths is the convenience it provides in packaging and distributing applications, their dependencies, and environments. Docker, Inc. provides an open-source container registry that many use as starting points for their containers, allowing one to create new containers that build on the work of others. However, the convenience of the Docker ecosystem comes at the cost of increasing the difficulty of knowing which applications and dependencies are within a Docker container, allowing administrators to unknowingly grow their org’s entire attack surface.
 At Exodus Intelligence, we understand the priority of knowing whether containerized applications are vulnerable, so that steps can be taken to mitigate and reduce overall risk. To this end, we are pleased to announce our partnership with Twistlock—the leader in securing containerized applications, and noted as one of the “Top 20 Cyber Security firms to watch in 2016” by Dark Reading. In this partnership, Exodus Intelligence Zero-Day metadata becomes an integral intelligence source within Twistlock applications.
At Exodus Intelligence, we understand the priority of knowing whether containerized applications are vulnerable, so that steps can be taken to mitigate and reduce overall risk. To this end, we are pleased to announce our partnership with Twistlock—the leader in securing containerized applications, and noted as one of the “Top 20 Cyber Security firms to watch in 2016” by Dark Reading. In this partnership, Exodus Intelligence Zero-Day metadata becomes an integral intelligence source within Twistlock applications.
With the addition of Exodus’ Zero-Day metadata, Twistlock customers will be able to scan their containers, both at rest and at runtime, and identify applications and packages which are known to contained unpatched vulnerabilities. Users may then take action to mitigate their exposure and contain their risk until the vendor releases a patch. With Exodus metadata, insight is provided into never-before-seen vulnerabilities before attackers are aware of them, and before most existing security solutions are even aware.
The following screenshots from the Twistlock application illustrates the integration of new Exodus Zero-Day metadata. Packages containing the Exodus Zero-Day vulnerabilities will be detected and highlighted in the UI. Users who wish to obtain more information about the vulnerability will be redirected to the Exodus interface, highlighted in the second screenshot, allowing them to explore the vulnerability and purchase detailed reports, exploit software and packet traces.
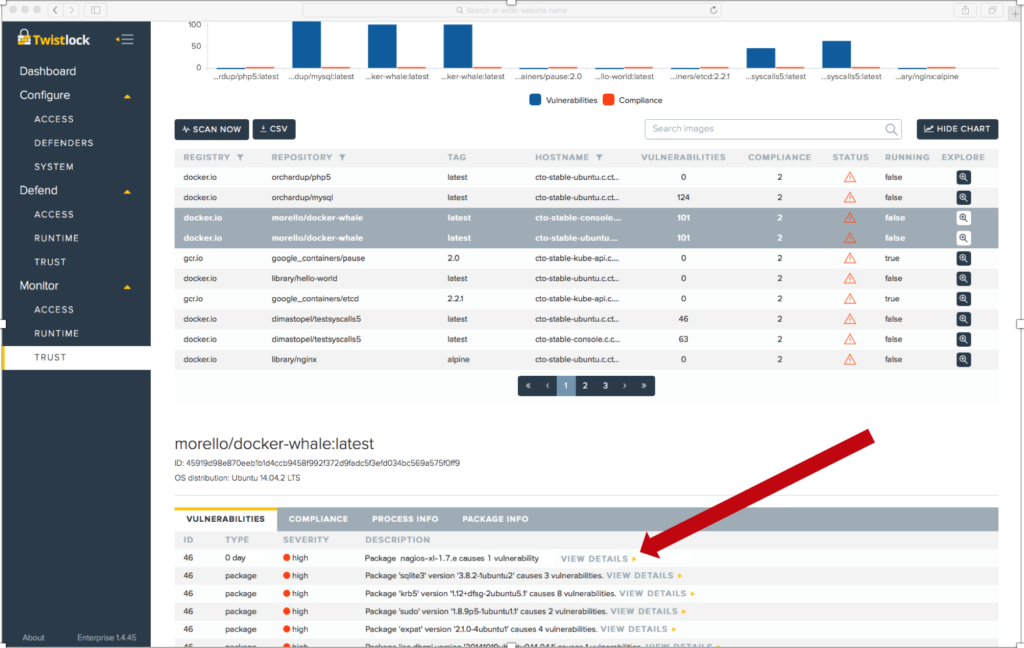
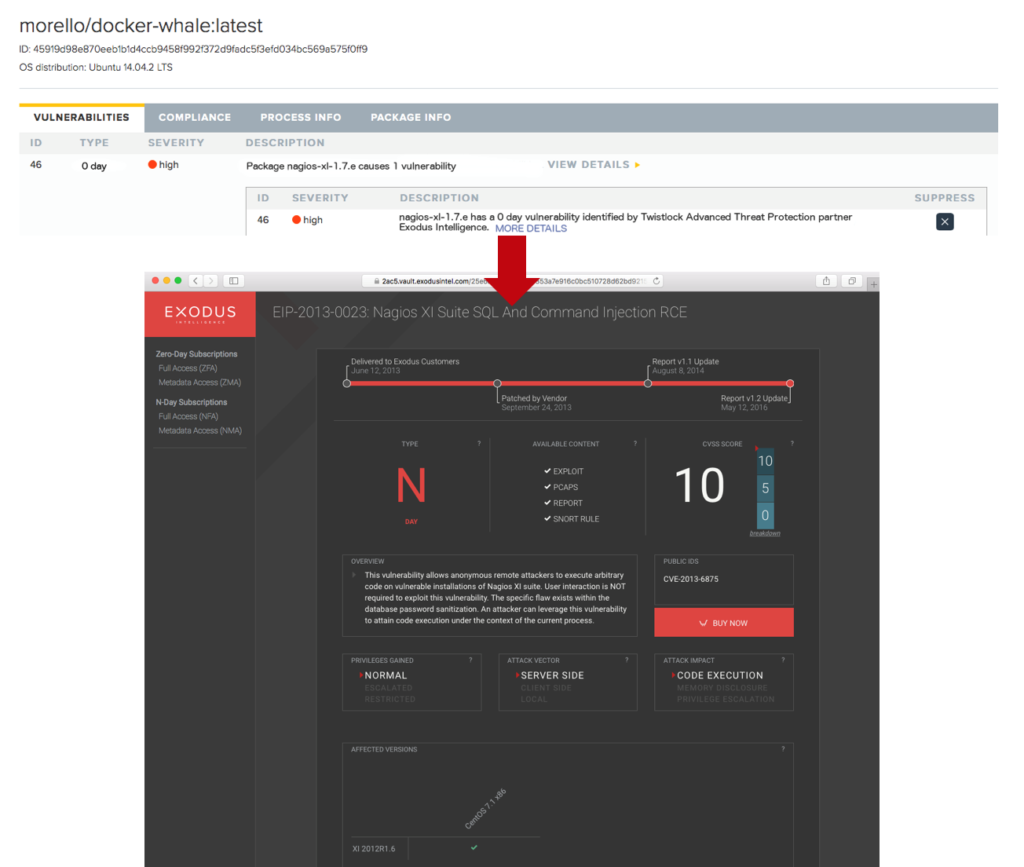
The integrated solution is expected to be available from Twistlock in Q4 of 2016. Contact us now for more information or visit Twistlock at BlackHat 2016—Booth #IC17—where you can see a demo preview of Exodus with Twistlock.
Together, Exodus and Twistlock are taking container security to the next level.
Click here to learn more about Twistlock and Exodus Intelligence.
[1]Stats from 2016 State of the Cloud Survey. http://www.rightscale.com/blog/cloud-industry-insights/cloud-computing-trends-2016-state-cloud-survey
