Vulnerability Assessment Course – Summer 2024
This course introduces vulnerability analysis and research with a focus on Ndays. We start with understanding security risks and discuss industry-standard metrics such as CVSS,
Exodus ensures that each and every discovered vulnerability is relevant, reliable, and well-documented before we disclose the issue to the appropriate vendor for remediation.
This course introduces vulnerability analysis and research with a focus on Ndays. We start with understanding security risks and discuss industry-standard metrics such as CVSS,
This 4 day course is designed to provide students with both an overview of the Android attack surface and an in-depth understanding of advanced vulnerability
This 4 day course is designed to provide students with both an overview of the current state of the browser attack surface and an in-depth
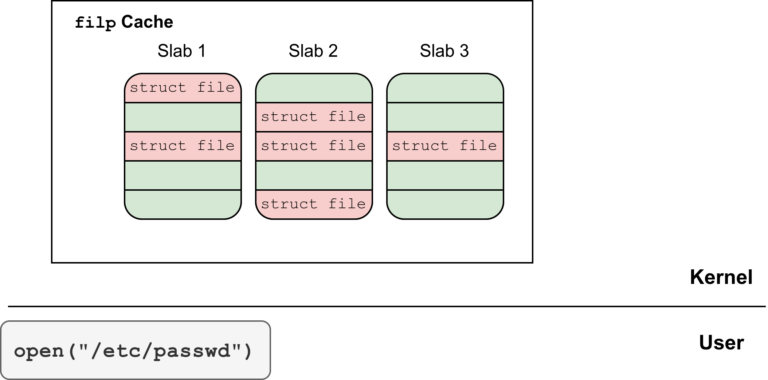
By Oriol Castejón Overview This post discusses a use-after-free vulnerability, CVE-2024-0582, in io_uring in the Linux kernel. Despite the vulnerability being patched in the stable kernel in December
